An email SPF record is basically a public guest list for your domain. It’s a simple text record you add to your DNS that tells the world which IP addresses are officially allowed to send emails on your behalf. Think of it as your first line of defense against scammers trying to impersonate you, making sure your real emails actually hit the inbox. So, if you've been wondering what is spf record, this guide will explain it all.
Unpacking the Basics of SPF Records
Imagine your company's domain is an exclusive VIP club. Every single spf email you send is a guest showing up at the door. An SPF record is the bouncer's official, approved guest list.
When an email from your domain arrives at someone's inbox (the club), their mail server (the bouncer) glances at the sender's IP address and checks it against your public SPF list. If the IP is on the list? Welcome in. If not, that email looks suspicious and might get flagged as spam or rejected on the spot.
This simple check is the heart of spf email security. It answers one critical question for every receiving server out there: "Is this message really from who it says it's from?" Without it, anyone could send an email pretending to be from your domain, a sneaky tactic called spoofing. To define spf record in simple terms, it's a validation system.
Why Is an SPF Record So Important?
At its core, the Sender Policy Framework (SPF) is all about building trust. It's a non-negotiable piece of the puzzle for your brand’s reputation and email deliverability. Here’s a quick look at why it matters so much:
- It Stops Email Spoofing: An spf record makes it way harder for bad actors to impersonate your domain, protecting your customers and partners from dangerous phishing attacks. This is a key part of spf security.
- It Boosts Your Deliverability: Mailbox providers like Gmail and Outlook trust authenticated emails more. Having valid spf records signals that you're a legitimate sender, which is a massive help to avoid emails going to spam.
- It Protects Your Brand Reputation: By shutting down unauthorized emails, you keep your domain from being tied to spam or scams, which can tank your sender reputation fast.
This infographic breaks down how that single, simple record pulls off all these security benefits.
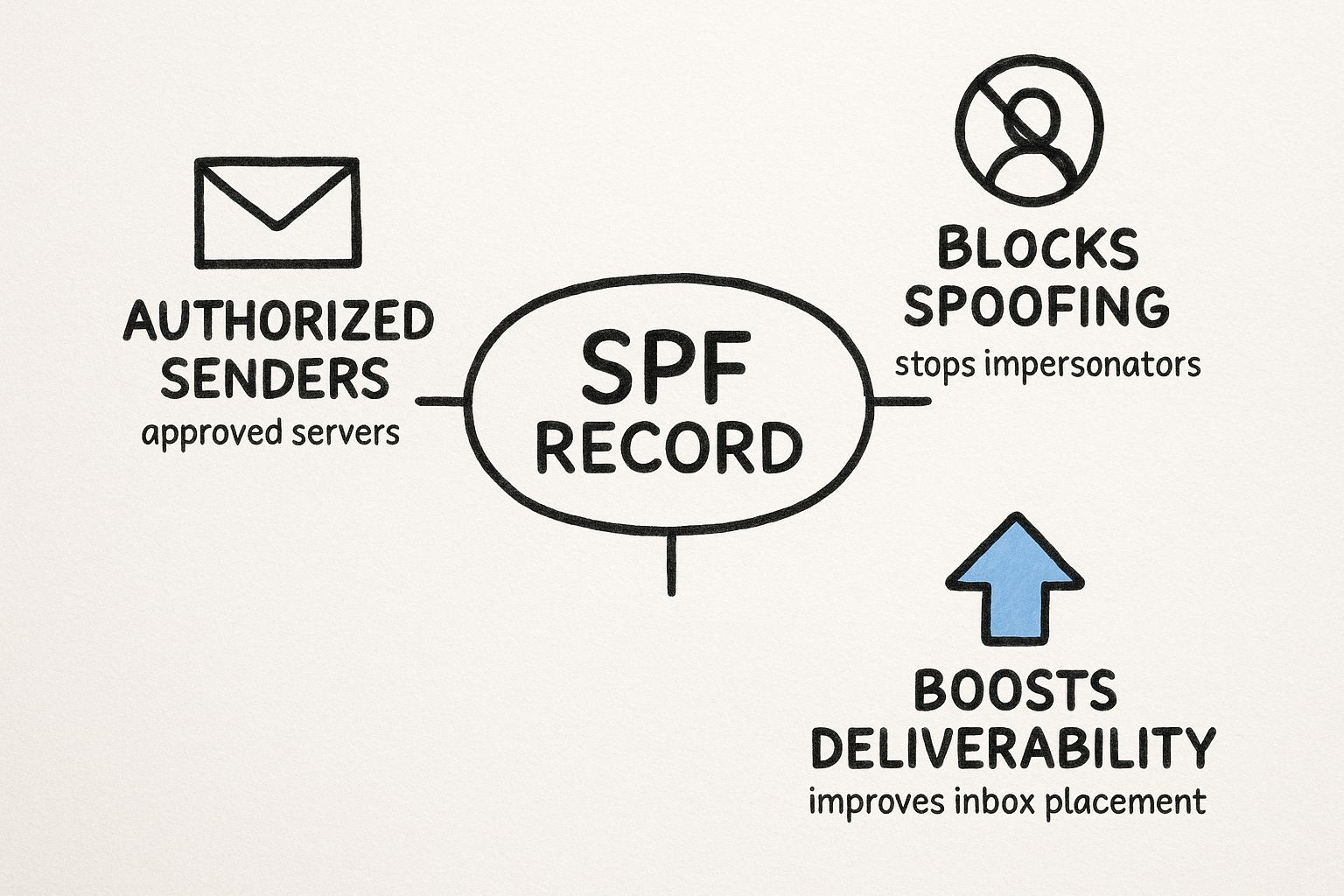
As you can see, it all starts with authorizing your legitimate senders. That simple step directly blocks spoofing, which in turn gives your deliverability a healthy boost.
To give you a clearer picture, here’s a quick breakdown of the parts that make up a typical mail spf record.
Quick Overview of SPF Record Components
This table breaks down the core components of a typical spf record, helping you quickly understand its structure and purpose.
Understanding these pieces is the first step to getting your own email spf record set up correctly and protecting your domain.
A Foundational Layer of Email Security
The Sender Policy Framework first showed up back in 2004, created specifically to fight domain impersonation. Its use has exploded as email-based threats have become a daily headache for businesses.
The numbers don't lie. By 2023, studies found that about 54.1% of the top one million domains had an SPF record in place, a huge jump from previous years. You can dig into more of the data in the full research on email authentication adoption.
So, when you ask, "what is an spf record for email?" the answer is straightforward. It's an essential, non-negotiable part of your email setup that proves you are who you say you are and keeps your communication channels secure. Many in SPF IT consider this a baseline requirement.
Decoding the Language of Your SPF Record
At first glance, an email spf record looks like a cryptic line of code reserved for network engineers. The good news? It's actually a simple, logical sentence written in a specific language. Once you get the hang of the basic vocabulary and grammar, you can read any mail spf record and know exactly what permissions it’s giving out.
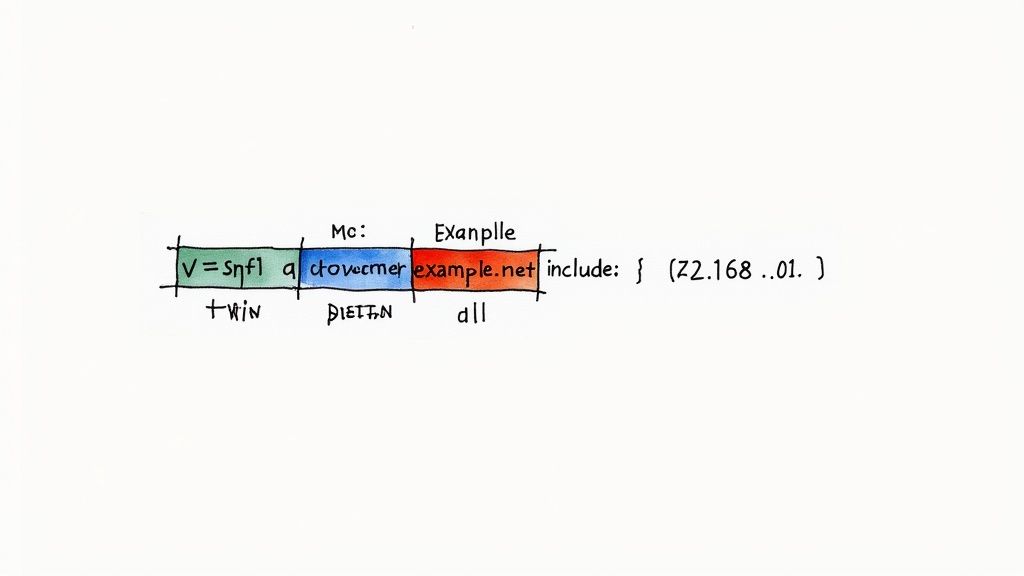
Think of your DNS spf record as a sentence that always starts the same way: with v=spf1. This is just a version tag, telling receiving mail servers, "Hey, this is an SPF record, and it's version 1." Answering the question of "what is spf email" starts with understanding this syntax.
Everything after that tag is a set of rules that defines your approved sender list. These rules are built from two key ingredients: mechanisms and qualifiers.
Understanding SPF Mechanisms
Mechanisms are the heart of your spf record. They specify which servers or IP addresses are actually allowed to send email for your domain. Each mechanism is like a specific instruction for the receiving server to check against.
Let's break down the most common ones you'll see.
a: Theamechanism is super simple. It gives the green light to the server associated with your domain's A record—basically, the main IP address of your website. Think of spf record a as saying, "The server hosting my website is allowed to send email." The spf a mechanism is a common starting point.mx: This one authorizes the mail servers listed in your domain's MX records. Since these are the servers set up to receive your email, it's pretty common for them to also be the ones sending it.ip4/ip6: These are the most direct instructions. They authorize a specific IPv4 or IPv6 address to send mail on your behalf. It’s like putting a specific person's name on a guest list—no room for confusion.include: Theincludemechanism is a lifesaver when you use third-party services like Google Workspace or Mailchimp. It tells the receiving server to go check the SPF record of another domain and trust whoever they've approved. It's like telling the bouncer, "Anyone on Google's list is cool with me, too."
By mixing and matching these mechanisms, you create a comprehensive spf record for domain security that covers all your legitimate sending sources.
The Role of Qualifiers
So, mechanisms define who can send email. But what about everyone else? That's where qualifiers come in. They tell receiving servers what to do when an email arrives from a source that isn't on your approved list.
While each mechanism can have a qualifier, the most important one is at the very end, paired with the all mechanism. This acts as the final rule for any sender not mentioned before.
Key Takeaway: The
allmechanism at the end of your SPF record is the most critical part. It acts as the default rule for any sender not explicitly listed, defining your domain's security policy.
There are four main qualifiers, each signaling a different level of strictness.
Choosing between -all (hard fail) and ~all (soft fail) is a huge decision in spf email security. A hard fail offers the strongest protection by telling servers to flat-out reject unauthorized mail. A soft fail is more lenient, often used when you're still figuring out all your sending sources and don't want to accidentally block something legitimate.
The whole spf vs all debate really boils down to how confident you are in your list of approved senders.
To really get a grip on this, it helps to dive a bit deeper into the core concepts. You can learn more about the technical side of things in our full guide on the Sender Policy Framework (SPF). Nailing these elements is central to what SPF in cyber security is all about.
How to Create an SPF Record for Your Domain
Building an SPF record is less about technical wizardry and more about being a good detective. Think of it like this: you're the bouncer for your domain's email, and your job is to create an exclusive guest list. Anyone not on that list? They don't get in.
This guest list is your spf record, and it needs to name every single service you've authorized to send email for you. It might sound like a hassle, but getting this right is the foundation of solid deliverability. It's what keeps your legitimate emails out of the spam folder and stops scammers from spoofing your domain.
Let's break down exactly how you build this thing from scratch, step-by-step.
Step 1: Identify All Your Sending Sources
Before you even think about writing your record, you need to map out every single platform that sends emails using your domain. This is the most crucial step, and it’s where most people go wrong. Forgetting just one service means its emails could get blocked.
Go on a hunt and catalogue everything. Seriously, everything. Your list will probably include:
- Your main inbox provider: Think Google Workspace or Microsoft 356. This is the obvious one.
- Email marketing tools: Mailchimp, SendGrid, Constant Contact—whatever you use for newsletters.
- Transactional email services: The platforms that send automated receipts, password resets, and shipping updates, like Postmark or Amazon SES.
- CRMs and sales tools: HubSpot, Salesforce, or any outreach tool your sales team lives in.
- Your own servers: Does your website's contact form send emails directly? That counts. Any application server sending notifications? That counts too.
Get this list right, and you’re halfway there. A complete inventory is the blueprint for an accurate SPF record.
Step 2: Gather the SPF Info from Each Source
With your list in hand, it's time to collect the magic words from each provider. Every service that sends email for you will tell you exactly what piece of text they need in your spf record. You just have to find it in their help docs.
You're generally looking for one of two things:
- An
includemechanism: This is the most common. A provider will give you a domain snippet to add, likeinclude:_spf.google.comorinclude:sendgrid.net. It's basically a shortcut that points to their own list of approved servers. - IP addresses (
ip4orip6): Some services, particularly older systems or your own web servers, might give you a specific IP address to list directly.
Work your way down your inventory, visiting the "Email Authentication" or "DNS Settings" section of each service's documentation. Copy and paste their required values into a notepad. Precision matters here.
Step 3: Assemble Your SPF Record
Okay, you've got all the ingredients. Now it's time to cook. Every SPF record is just a single string of plain text that lives in your domain's DNS settings.
It follows a simple formula:
v=spf1 [sender #1] [sender #2] [sender #3] ... -all
Let's build one for a fictional company. Say they use Google Workspace, Mailchimp, and have a web server with a dedicated IP address.
- Start with the version: Every record begins with
v=spf1. - Add Google Workspace:
include:_spf.google.com - Add Mailchimp:
include:servers.mcsv.net - Add the web server:
ip4:192.0.2.1 - Finish with a rule:
-all
String it all together, and you get this:
v=spf1 include:_spf.google.com include:servers.mcsv.net ip4:192.0.2.1 -all
That one line tells every receiving mail server on the planet, "Only trust emails from these sources. If it comes from anywhere else, reject it." That -all at the end is the "hard fail" instruction—it's what gives your policy teeth.
Putting together a solid spf record is a non-negotiable part of modern email security. For a deeper dive into the whole setup, check out our guide on the tech setup for cold email including SPF, DKIM, and DMARC.
Once you have your final SPF string, the last step is to publish it as a TXT record in your domain's DNS. That's it. You've just activated a powerful layer of protection for your brand.
Avoiding Common SPF Record Mistakes
Setting up an SPF record is a massive win for your email security, but a single misstep can accidentally get your own emails blocked or leave your domain wide open to spoofing. Think of it like a high-tech security system for your house—if you connect one wire incorrectly, the whole system might fail when you need it most. Knowing the common pitfalls is just as important as knowing how to build the record in the first place.
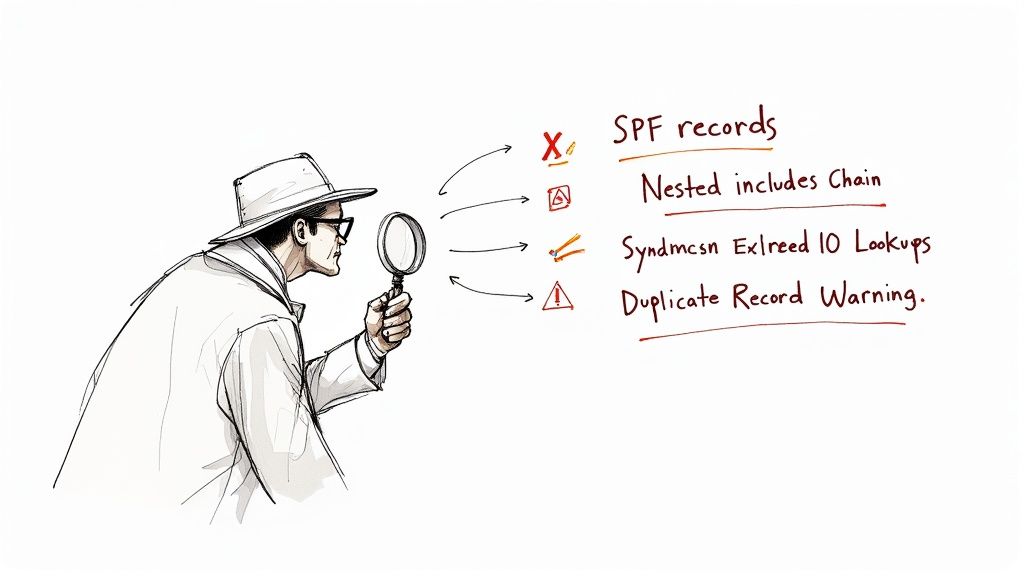
It’s an all-too-common story: a company sets up its mail spf record, breathes a sigh of relief, and then moves on, completely unaware that small errors are sabotaging their efforts. It's a bigger problem than you might think. Recent studies show that even with SPF adoption on the rise, around 13% of published SPF records have deal-breaking errors, usually from exceeding lookup limits or simple typos. You can read the full research about these SPF findings to see just how widespread these issues are.
Let’s pull back the curtain on the most frequent mistakes so you can steer clear and keep your SPF email authentication working like a charm.
The 10 DNS Lookup Limit
This is the big one. It's easily the most notorious and misunderstood rule in the SPF world.
Imagine a detective investigating a case, but they're only allowed to make 10 phone calls to verify alibis. That's exactly how an email SPF record works. Every time a receiving mail server has to check an include, a, mx, or redirect in your record, it counts as one of those "phone calls," or a DNS lookup.
If your record forces the server to make an 11th call, the check fails. Instantly. This triggers a "permerror" (permanent error), which basically invalidates your entire SPF setup for that email and often sends your legitimate message straight to the spam folder.
Key Insight: The fastest way to blow past the 10-lookup limit is with nested
includestatements. Oneincludefor a service might point to their SPF record, which contains even moreincludestatements. It creates a chain reaction that eats up your lookup budget in a hurry.
To dodge this bullet, you have to audit your DNS SPF record regularly. If you can, "flatten" it by swapping out include mechanisms for specific, static IP addresses.
Publishing Multiple SPF Records
This is a fatal flaw for SPF security, and there's no wiggle room here. You can only have one SPF record per domain. Period.
If a receiving server looks up your domain and finds two or more TXT records starting with v=spf1, it will immediately throw a permerror and stop the check. It won't try to guess which one is correct.
This usually happens when a team member adds a new email service (like a marketing platform) and, instead of adding it to the existing record, just creates a brand-new one.
v=spf1 include:_spf.google.com -allv=spf1 include:sendgrid.net -all
v=spf1 include:_spf.google.com include:sendgrid.net -all
Always, always update your single, authoritative SPF record for domain health. Never add a second one.
Simple Syntax and Formatting Errors
Even the smallest typo can bring the whole thing down. SPF records are technical strings of text, and they demand perfection. Some of the most common slip-ups are surprisingly simple:
- Missing Spaces: Forgetting a space between mechanisms is a classic. For example:
include:_spf.google.cominclude:sendgrid.net. - Extra Quotation Marks: Some DNS providers automatically wrap your TXT value in quotes. If you add your own quotes inside the record, it can cause the validation to fail.
- Wrong Qualifier: Accidentally using
~all(which suggests a softfail) when you really meant-all(a hardfail) significantly weakens your security policy. It tells servers to be suspicious but not to outright reject fakes.
Getting into a rhythm of auditing your setup is the best way to catch these subtle yet destructive errors. To see how SPF fits into the bigger picture of a healthy sending reputation, check out our complete email deliverability checklist. By sidestepping these common mistakes, you’ll ensure your spf record gives you the solid protection it was designed for.
SPF in Cyber Security and Its Role with DKIM and DMARC
While an email SPF record is a crucial piece of the email security puzzle, relying on it alone is like building a fortress with only one wall. It answers a single, important question: "Is this email coming from an approved server?" But that's where its job ends.
It won't tell you if the message itself was tampered with in transit, and it doesn't give receiving servers instructions on what to do when something looks fishy. This is where its partners, DKIM and DMARC, step in to complete the picture. SPF in cyber security is a team player.
Think of your email authentication setup as a three-legged stool—if one leg is missing, the whole thing becomes unstable. Each protocol adds a unique, essential layer of protection, and they work together to build a strong defense against today's sophisticated phishing and spoofing attacks.
The Three Pillars of Email Authentication
To really lock down your domain, you need a layered defense. An SPF record is your first line, but DKIM and DMARC provide the critical depth that makes your setup truly secure.
SPF (Sender Policy Framework): As we've covered, this is your security "guest list." It verifies that any email claiming to be from your domain was sent from an IP address you've personally authorized. Its main role is to shut down basic domain impersonation right at the source.
DKIM (DomainKeys Identified Mail): Think of this as the "tamper-proof seal" on a package. DKIM attaches a unique digital signature to every outgoing email. The receiving server can check this signature to confirm that the message—down to every last word—hasn't been altered. If anything changes, the seal is broken.
DMARC (Domain-based Message Authentication, Reporting & Conformance): This is the "enforcement policy," or the head of security. DMARC looks at the results from SPF and DKIM and tells receiving servers exactly what to do if an email fails either check. It also sends back valuable reports, giving you a clear view of who is sending mail using your domain.
The combination of SPF security and its partners is what separates a basic email setup from a properly protected one.
How SPF, DKIM, and DMARC Work Together
Let’s use an analogy. Imagine you're sending a highly sensitive package.
The SPF record is like ensuring the package is picked up by an approved, official courier—you're verifying the sender's origin.
DKIM is the sealed, tamper-evident tape you wrap around the box. It’s proof that nothing inside has been touched or swapped out.
DMARC provides the final instructions for the recipient: "If the courier is unofficial OR if the seal is broken, reject the delivery on the spot. No exceptions."
Without all three, you leave dangerous gaps open for attackers. An email might pass an SPF check (coming from a valid server) but have its contents maliciously changed mid-journey. Or, an email could fail both checks, but without a DMARC policy, the receiving server might just flag it as spam instead of blocking it completely.
To help you visualize how these three protocols fit together, here’s a quick comparison.
Email Authentication Protocols Compared
This table breaks down how SPF, DKIM, and DMARC each tackle a different part of the problem, creating a layered defense that's much stronger than any single protocol.
Each protocol plays a vital role, but their combined strength comes from working in harmony to validate an email's legitimacy from multiple angles.
The real power of this trio is alignment. DMARC checks to see if the domain in the "From" address (the one your recipient sees) matches the domains verified by SPF and DKIM. This simple alignment check is what shuts down sophisticated spoofing attacks that an SPF record check alone would miss.
This layered approach is no longer optional; it's the industry standard. The rapid adoption of DMARC proves it—it's a protocol built specifically to leverage the power of SPF and DKIM.
Between 2023 and 2025, DMARC adoption among top global domains is projected to have surged by 75%, from 27.2% to 47.7%. More importantly, the use of strict enforcement policies like "quarantine" and "reject" has increased by 50%.
Ultimately, a mail SPF record is an indispensable starting point. But for comprehensive protection, it must be paired with DKIM and DMARC.
To learn more about the second pillar of this security trio, check out our guide on DKIM: https://www.plusvibe.ai/blog/dkim-records. And remember, email authentication is just one part of domain security. Securing your web traffic is just as important, and you can learn more about how to configure an SSL certificate to get a complete picture.
Of course. Here is the rewritten section, crafted to sound like a human expert.
Common Questions About SPF Records (Answered)
Even after you get the hang of SPF, some practical questions always seem to pop up when you're in the trenches, trying to get it configured just right. Let's walk through some of the most common ones I hear, so you can tackle your own SPF record setup with confidence.
How Can I Check My Current SPF Record?
Checking your domain's SPF record is a must-do first step, and thankfully, it's dead simple. You don't need to be a DNS wizard to pull this off.
There are a bunch of great, free online tools out there like MXToolbox or Google's Admin Toolbox built for exactly this. Just head over to one of them, pop your domain name into their SPF checker, and hit go. The tool will do a quick DNS SPF record lookup and spit out what it finds.
More importantly, it'll flag common screw-ups—like syntax errors, having more than the 10-lookup limit, or the cardinal sin of publishing multiple SPF records. This quick check is your best friend for diagnosing deliverability headaches before they get out of hand.
What's the Real Difference Between ~all and -all?
This is probably one of the most critical choices you'll make in your record. The little character at the end—~all (SoftFail) or -all (HardFail)—is your instruction to the world's email servers on how to treat emails that fail your SPF check. The whole SPF vs all debate really comes down to this: how strict do you want to be?
Here's how to think about it:
-all(HardFail): This is you telling receiving servers, "If the email comes from a server not on my list, drop it. It's not from me. Don't even let it in the door." This is the gold standard and what you should aim for. It offers the strongest possible protection against someone spoofing your domain.~all(SoftFail): This is a more gentle suggestion. It says, "Hey, this email is from a server I don't recognize. It's probably spam, so you should mark it as suspicious, but I'll let you make the final call." People often use this when they're first setting up SPF and are still trying to map out every single service that sends email on their behalf. It's a "just in case" setting to avoid blocking legitimate mail by mistake.
Bottom line: -all is the destination. A HardFail gives clear, unambiguous instructions to block imposters, which is exactly what you want for solid SPF email security.
Expert Insight: It might feel safer to start with a SoftFail (
~all), but remember, you're leaving the door open for interpretation. A HardFail (-all) slams that door shut on spammers and gives you a clear, enforceable policy that maximizes your domain's protection.
Can I Have More Than One SPF Record for a Domain?
Nope. Never. Absolutely not.
This is one of the most common and most damaging mistakes people make. Your domain must have only one SPF record. If you publish multiple TXT records starting with v=spf1, you've just broken your SPF authentication for good.
When a mail server looks up your domain, finding two or more SPF records creates a "PermError" (Permanent Error). The server has no idea which record to trust, so it trusts none of them. It won't try to merge them or pick the right one; it will simply fail the check. This completely defeats the entire purpose of having an SPF record for domain security.
If you need to authorize a new email provider, you have to edit your existing SPF record. Add the new service's include or IP address into that single, long string of text. Do not create a second record.
What Happens If My SPF Record Is Too Long?
This is another "gotcha" that trips a lot of people up. An SPF record has two limits, but the one you really need to watch is the 10 DNS lookup limit. The record also can't be longer than 255 characters in a single string, but that's less common to hit.
Every time you use a mechanism like include, a, mx, or redirect in your record, it counts as one lookup. The problem is that an include from a third-party service (like your email marketing tool) might contain other lookups inside of it, and they all count toward your total of 10.
If your record goes over this limit, it results in a PermError—the same permanent error you get from having multiple records. Your mail SPF record becomes invalid, and legitimate emails can start getting flagged or rejected. This happens all the time as companies add more and more third-party tools. The only way to stay on top of it is to check your record periodically with an online tool to make sure you're still under the limit.
Ready to stop worrying about email deliverability and start scaling your outreach? PlusVibe uses powerful AI to ensure your emails land in the primary inbox, engage prospects, and drive replies. Take control of your campaigns and see real results. Learn more about PlusVibe today!














































.jpeg)





























































